Keeping NZ businesses cyber-safe since 2002
Securecom brings a common-sense approach and practical advice to accelerate your cyber security posture.
Securecom Security Services
“Shockingly, nearly half of all cybercrime in New Zealand targets small businesses—where the average data breach costs around $173,000 NZD, enough to seriously threaten survival.”
Source: nsc.govt.nz 2024
At the heart of our Security Portfolio lies a powerful methodology – Measure → Remediate → Manage – this is a visual reminder that effective cybersecurity is not a one-off project, but an ongoing, adaptive cycle. This wheel symbolises Securecom’s full-spectrum approach: first assessing your current security stance, then fixing vulnerabilities, and finally delivering continuous, expert-led management. It’s a seamless loop of vigilance designed to keep your business environment secure, resilient, and always one step ahead.
Measure
We assess your security maturity to measure your current state and your exposure to cyber risks. These assessments cover security governance (including risk management, policy and process), technical security controls and vulnerability baselining.
Remediate
We take the findings from the assessments to develop a programme of remedial work to address any issues and fix any security gaps. Depending on your specific situation and the level of investment available, this may be a few project initiatives or a long-term programme of work.
Manage
We help you stay secure in the ever-changing cybersecurity landscape. Through continuous monitoring and alerting services from our Security Operations Centre, and ongoing advice and guidance from our Security Consultants, we help you continually improve to stay ahead of threats.
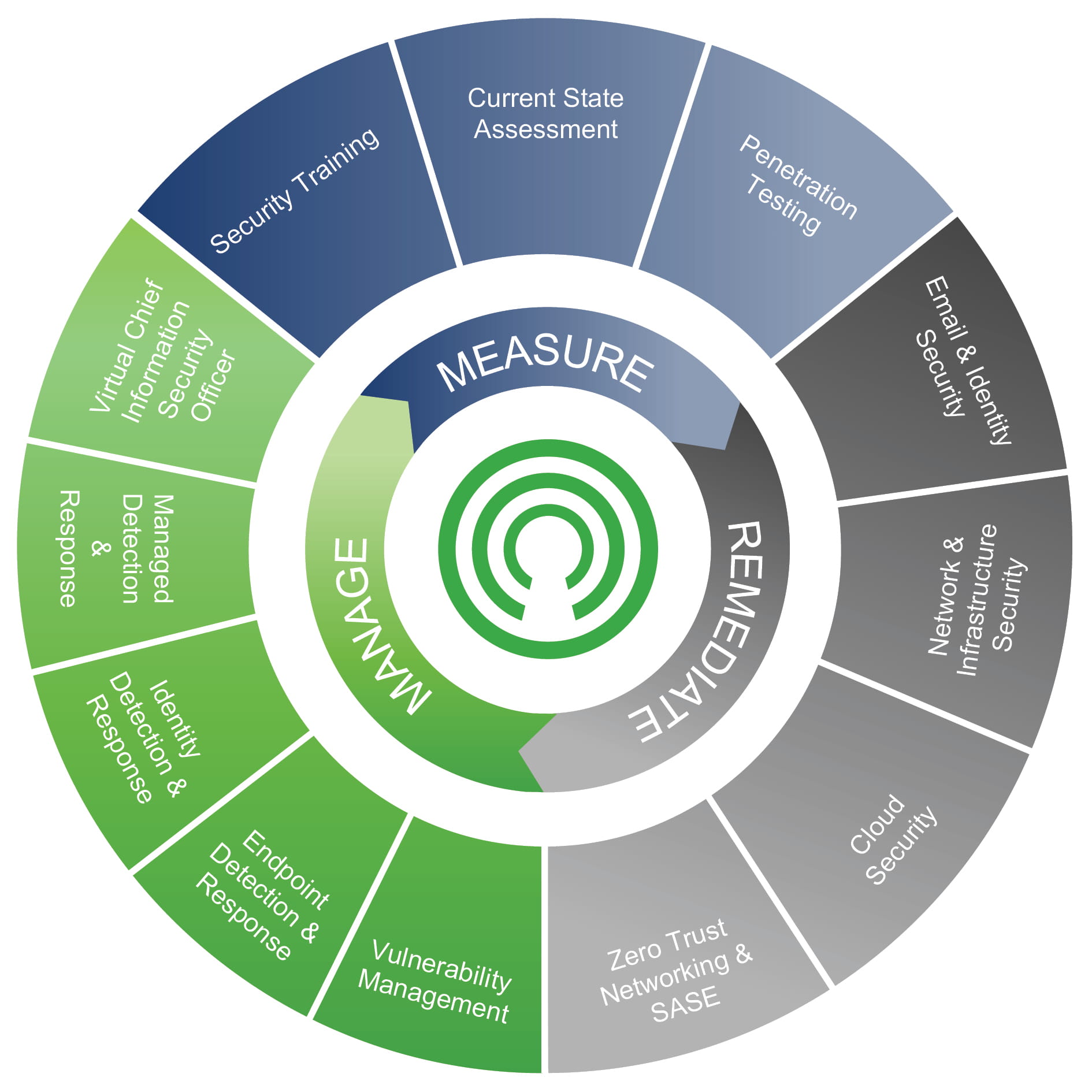
Our Security Portfolio
We offer a full suite of security services to give you the assurance from the Board down that you have the right blend of security controls, cultural awareness and governance to manage your cyber risk.
Measure
Security Training
Engage and equip your people with the knowledge and skills to spot, stop, and report threats before they escalate.
Current State Assessment
Comprehensive review of your current security posture to uncover vulnerabilities, prioritise fixes, and guide your cyber resilience strategy.
Penetration Testing (PTAAS)
Simulated real-world cyberattacks to expose weaknesses before criminals do, giving you the insight to strengthen defences.
Remediate
Email &
Identity Security
Advanced protection for email and user accounts, blocking phishing, credential theft, and unauthorised access to safeguard sensitive communications.
Network & Infrastructure Security
Layered security for networks, servers, and devices, defending against internal and external attacks that could disrupt operations.
Cloud
Security
End-to-end protection for cloud environments, ensuring compliance, resilience, and safe access to mission-critical data and applications.
Zero Trust
Networking & SASE
Implements “never trust, always verify” principles with secure, high-performance connectivity for users, devices, and applications everywhere.
Manage
Vulnerability Management
Ongoing identification, prioritisation, and remediation of weaknesses to reduce your organisation’s risk profile and maintain compliance.
Endpoint Detection & Response
Advanced device monitoring, threat isolation, and rapid remediation to prevent malware, ransomware, and targeted endpoint attacks.
Identity Detection & Response
Detects compromised user credentials early and blocks unauthorised access attempts to protect accounts and sensitive systems.
Managed Detection & Response
Proactive threat detection, rapid incident response, and continuous monitoring that protects your systems 24/7, ensuring threats are neutralised before damage occurs.
Virtual Chief Information Security Officer
On-demand strategic security leadership that shapes and executes a tailored cybersecurity roadmap without the cost of a permanent executive hire.
Why Securecom
With us, you know that IT is in reliable hands.
It’s time your IT delivered results
Have an IT specialist call you to discuss your technology needs.








